Hero Card: Third Parties With Access
© 2026 Sonrai Security. All rights reserved.
Overview
The Cloud Permissions Firewall (CPF) provides a simple and effective way to manage third-party access across all accounts within your AWS Organization.
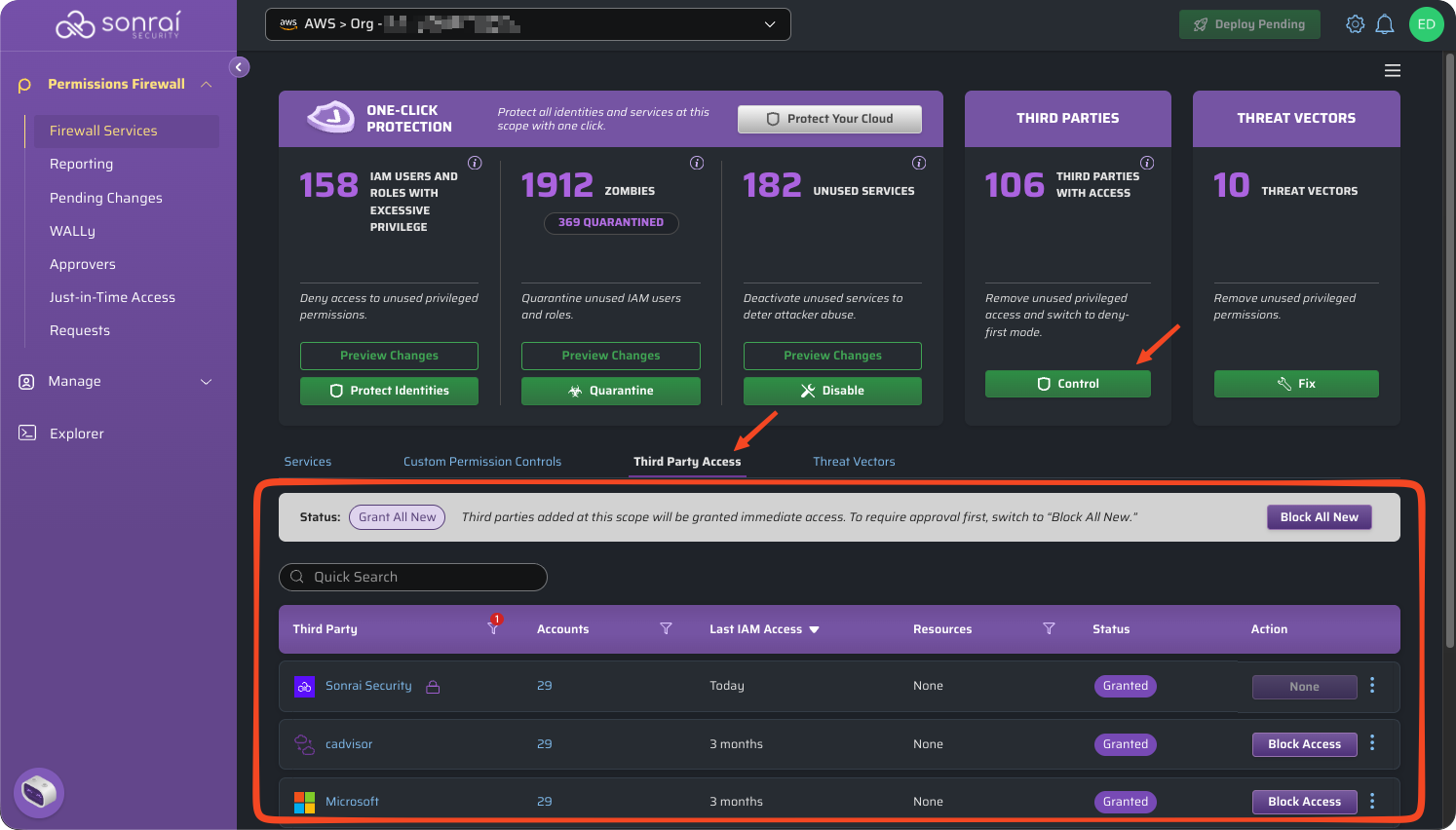
What is third-party Access into AWS Accounts?
Third-party access in this context refers to the ability of external entities such as vendors, partners, or contractors, to access resources and services within an AWS account. This access can be granted for various purposes, including system integration, support, and collaboration.
How does Sonrai know which accounts are considered third party?
The originating account for all trusted principals in either IAM Trust Relationships or Resource Policies are extracted and evaluated against the overall set of your known accounts. If the account in question is not within the list of your known accounts, and/or is on our list of known external identities, then it is deemed a third party.
Learn more about third party detection in CPF.
Why is it important to control third-party access?
Controlling third-party access is crucial for several reasons:
- Security: Unauthorized access can lead to data breaches, loss of sensitive information, and potential misuse of resources.
- Compliance: Many industries have regulatory requirements that mandate strict control over who can access data and systems.
- Risk Management: Limiting access reduces the risk of malicious activities and helps in maintaining the integrity of your cloud environment(s).
- Accountability: Monitoring and controlling access ensures that all actions can be traced back to the responsible party, aiding in auditing and accountability.
How does the Cloud Permissions Firewall manage third-party access?
The firewall leverages Resource Control Policies (RCPs) to manage access for third parties. This functionality will allow the Cloud Permissions Firewall to create control policies that block access to a number of resource types including S3, STS, KMS, SQS, Secrets Manager).
Further to that, you can disable or protect other services for those third party account(s) as needed!
Pre-Requisites
Enable RCPs (Required)
Resource Control Policies (RCPs) must be enabled in your AWS Organization to allow the Cloud Permissions Firewall to properly manage and secure third-party access.
Third Party Catalogue
The Cloud Permissions Firewall has a catalogue of third-party accounts that have access to your AWS accounts.
This catalogue is comprised of known vendors Sonrai has validated, as well as any custom third party vendors added by customers (once formally validated by Sonrai).
Examples of validated third parties within the firewall catalogue include:

CheckPoint
Census
Qualys
How Does It Work?
Within the Service page, manage external access to your cloud resources' privileged permissions to reduce risks associated with supply chain attacks and vendor-related breaches.
If completely disabling access to an entire third party is not viable, review each account role's policy to pare down to least privilege (where possible).
IAM Roles
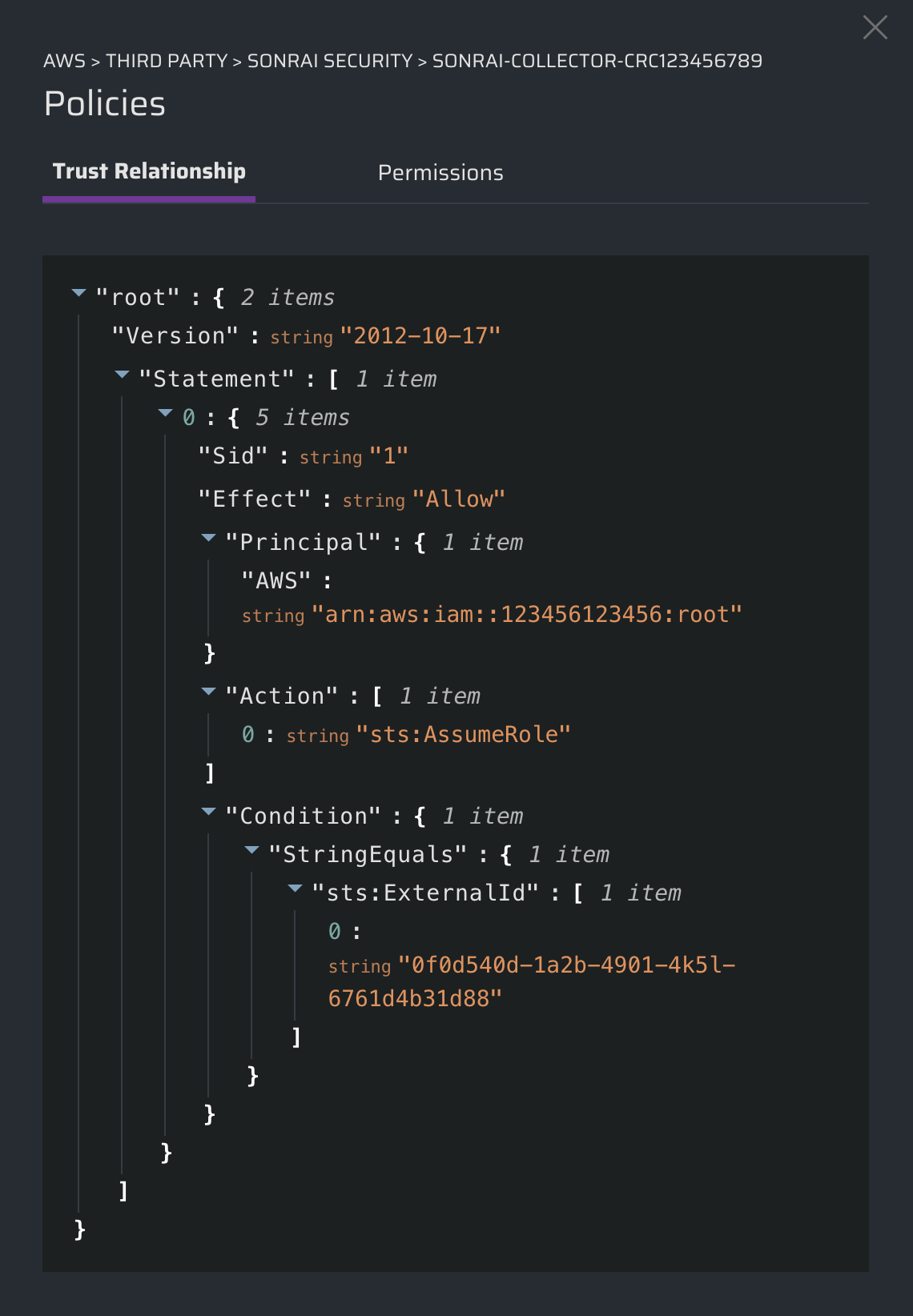
For identities (i.e. roles), third parties are identified using the account specified in the trust relationship attached to the IAM role. For example in the following trust relationship, 123456789123 would be the account evaluated.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789123:root"
},
"Action": "sts:AssumeRole"
}
]
}
Resource Policies
For direct resource access, the firewall will evaluate all the relevant resource policies for supported services and identify any third-party principals. In the following example of a KMS key policy, 123456788123, 123456789456 and 917634341498 would all be evaluated.
{
"Id": "key-consolepolicy",
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::123456788123:root"
]
},
"Action": "kms:*",
"Resource": "*"
},
{
"Sid": "Allow access for Key Administrators",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::123456789321:role/Admin"
]
},
"Action": [
"kms:Create*",
"kms:Describe*",
"kms:Enable*",
"kms:List*",
"kms:Put*",
"kms:Update*",
"kms:Revoke*",
"kms:Disable*",
"kms:Get*",
"kms:Delete*",
"kms:TagResource",
"kms:UntagResource",
"kms:ScheduleKeyDeletion",
"kms:CancelKeyDeletion"
],
"Resource": "*"
},
{
"Sid": "Allow use of the key",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::123456789456:role/DMS-Redshift-endpoint-access-role"
]
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
},
{
"Sid": "Allow attachment of persistent resources",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::123456789456:role/DMS-Redshift-endpoint-access-role"
]
},
"Action": [
"kms:CreateGrant",
"kms:ListGrants",
"kms:RevokeGrant"
],
"Resource": "*",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": true
}
}
}
]
}
Third Party Access Control
Within the firewall, there are six (6) states of third-party access. Each state change for a third party account requires you to redeploy the roles to apply the changes to your cloud.
| State Name | Description |
|---|---|
| Blocked | All third party access is blocked in all accounts [at the selected scope]. A third party is blocked at either Organization-level or a lower selected scope (i.e. OU, individual account, etc.) and those changes have been applied to your cloud. |
| Blocked (Pending) | The "Block Access" button is clicked for a third party table row entry resulting in the third party pending being blocked [at the selected scope]. These changes are visible within the Pending Changes list. |
| Partially Blocked | Some third party access is blocked in all accounts [at the selected scope]. A third party is disabled at a lower scope (i.e. OU, individual account, etc.) while other scopes under the Organization remain granted. |
| Partially Blocked (Pending) | There are a set of pending changes that when applied will lead to the third party being partially blocked [at the selected scope]. These changes are visible within the Pending Changes list. |
| Granted | All third party access is granted in all accounts [at the selected scope]. A third party is granted access at either Organization-level or a lower selected scope (i.e. OU, individual account, etc.) and those changes have been applied to your cloud. |
| Granted (Pending) | The "Grant Access" button is clicked for a third party table row entry resulting in the third party pending being granted access [at the selected scope]. These changes are visible within the Pending Changes list. |
Setting Default Behavior
When a new third party account is detected in CPF, a notification is sent out and the account is given the default status, as shown below. When first onboarded, CPF grants access for third party accounts in your cloud. You can change the default status for newly discovered third party accounts by clicking .
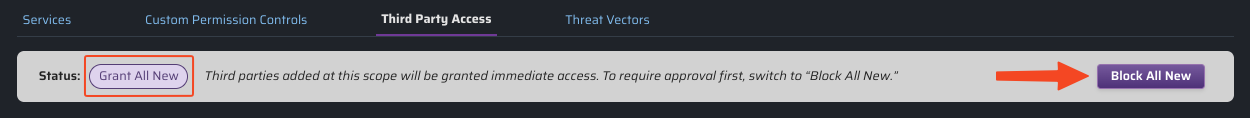
Grant All New
Third parties newly added at this scope will be granted immediate access. (This is the default behavior.)
Block All New
Third parties newly added at this scope will need to be granted access individually.
Any pre-existing third parties (at the time default status is toggled) will retain their current access status of Granted or Blocked.
Required Third Party Accounts
Rows with a lock icon are deemed to be necessary and cannot be blocked (Example: "Sonrai Security Third Party account access is required and cannot be blocked.")
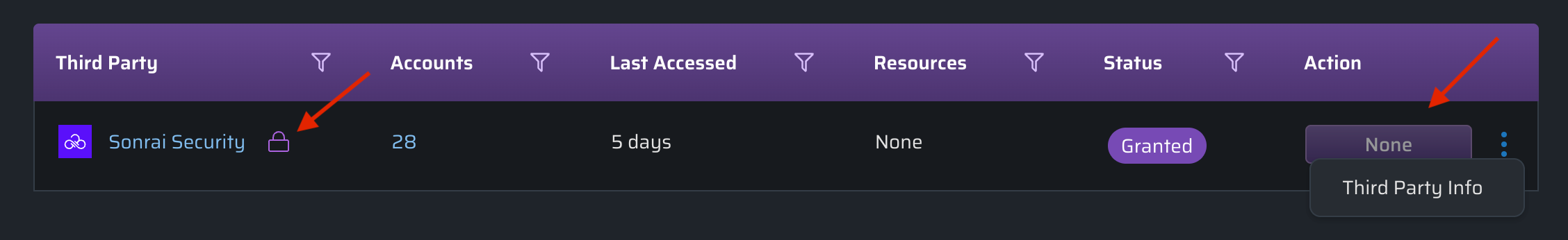
Though you cannot take any action on these locked rows, you can still view more information about the third party account. In this example, the accounts shown are not within the list of known accounts for the Organization and as such are deemed a third party account:
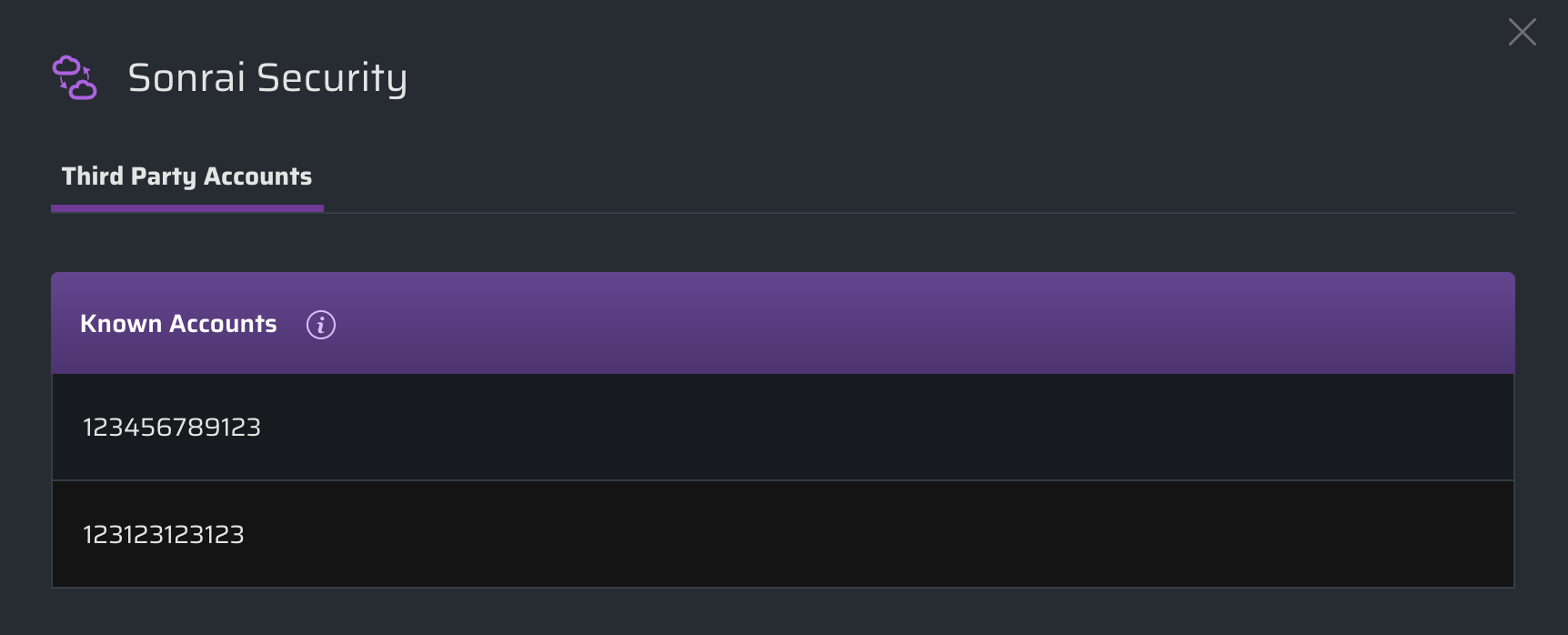
Reviewing Account Access
Click on the Accounts number within a row to view all accounts which that third party can access:
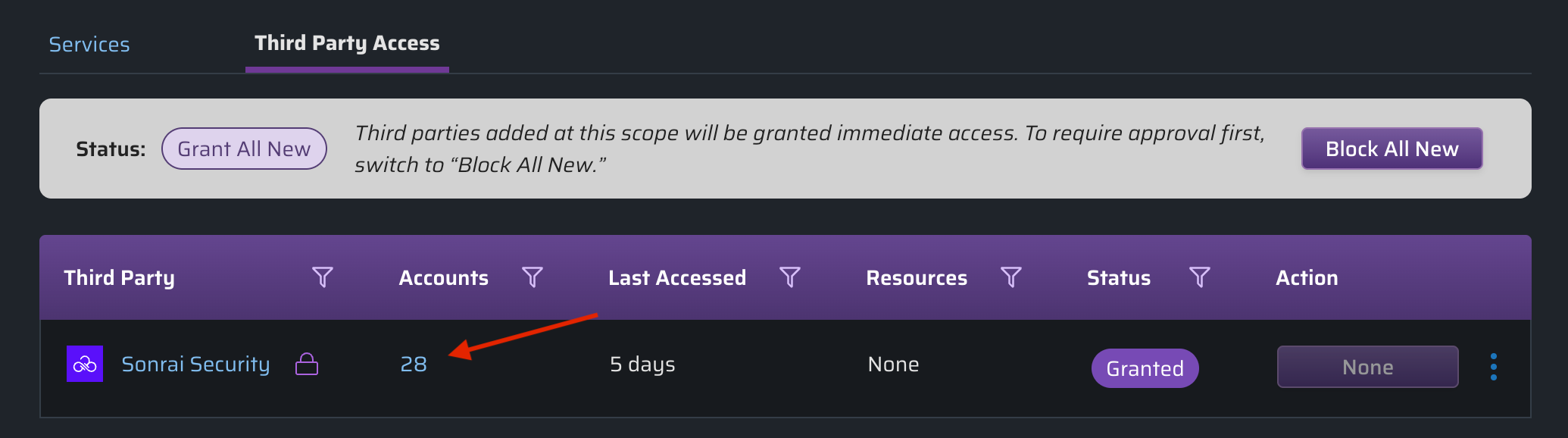
Expand an account to see a list of related roles, and view the that defines:
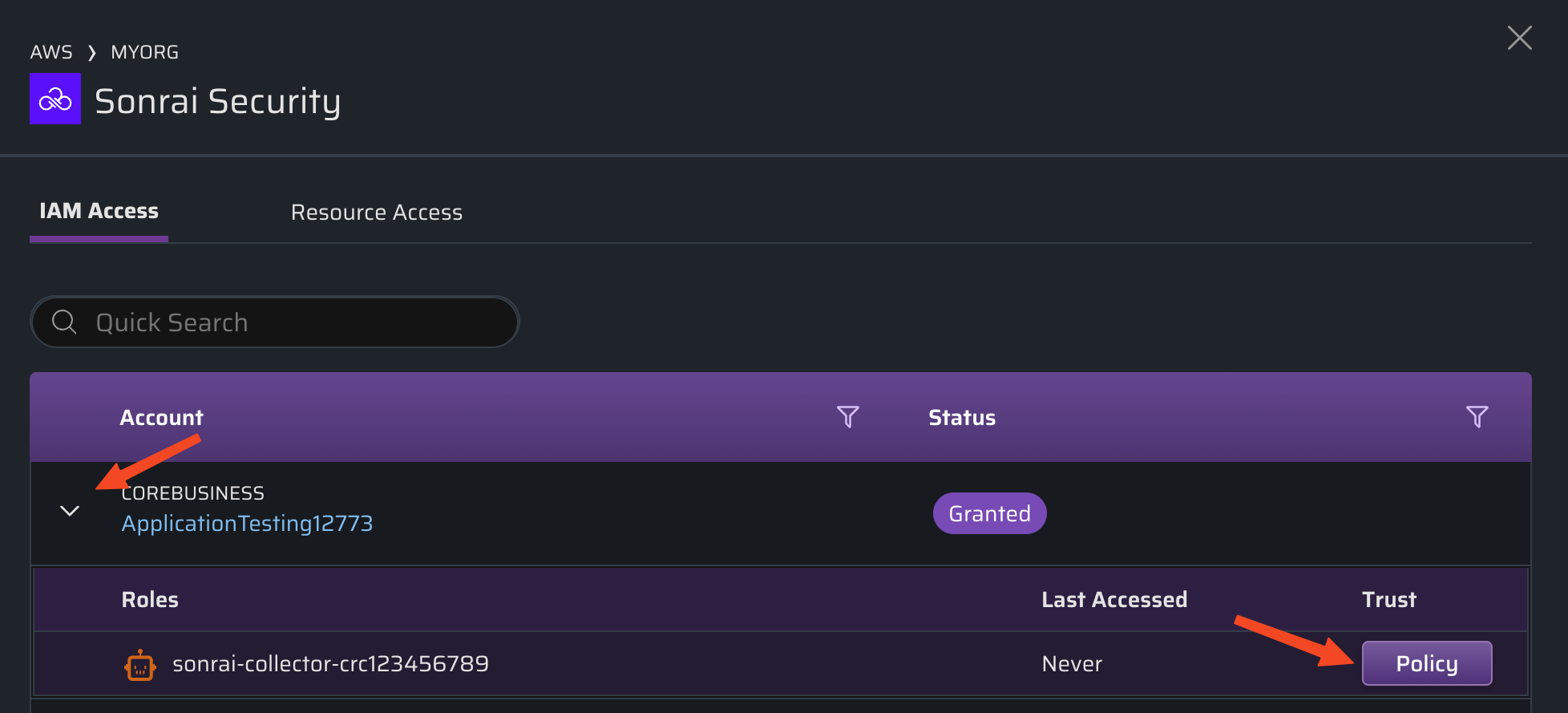
a) the trust relationship that enabled this access
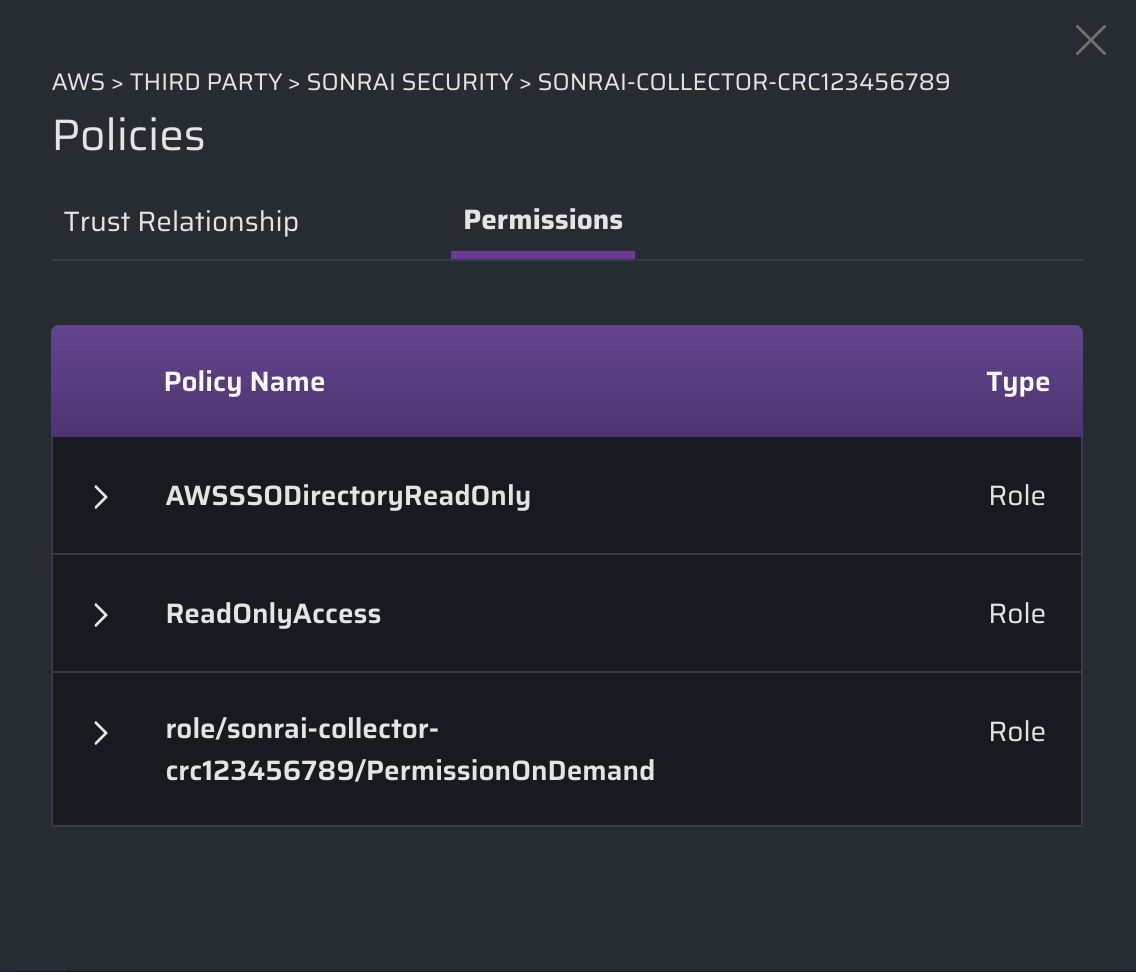
b) the level of permissions the third party can leverage (i.e. read, write, etc. actions)
Resource Access
Clicking on the resources number within the row will display all of the resources the third party account(s) can access:
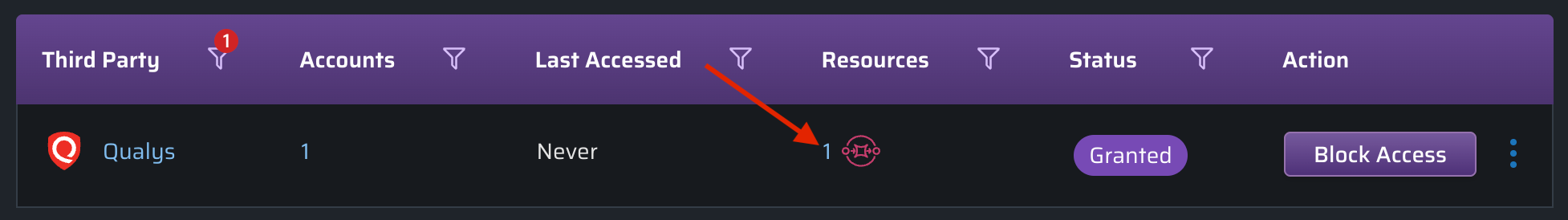
Click to view the associated resource control policy:
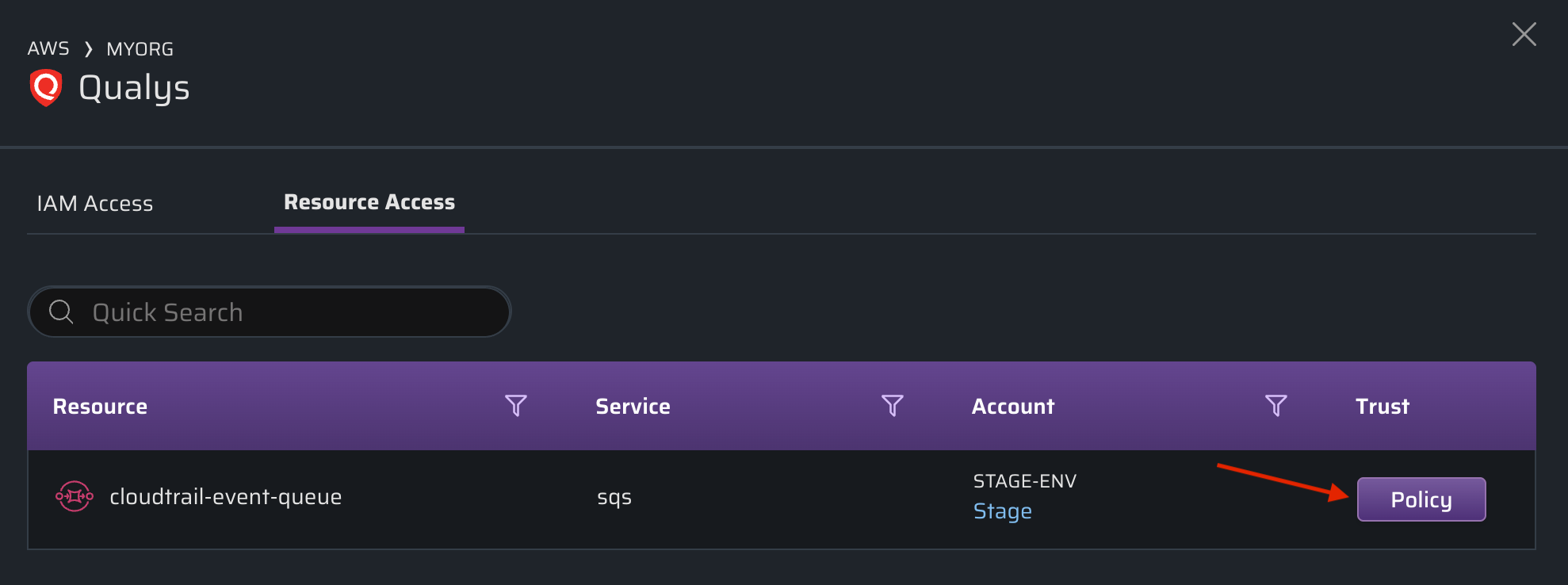
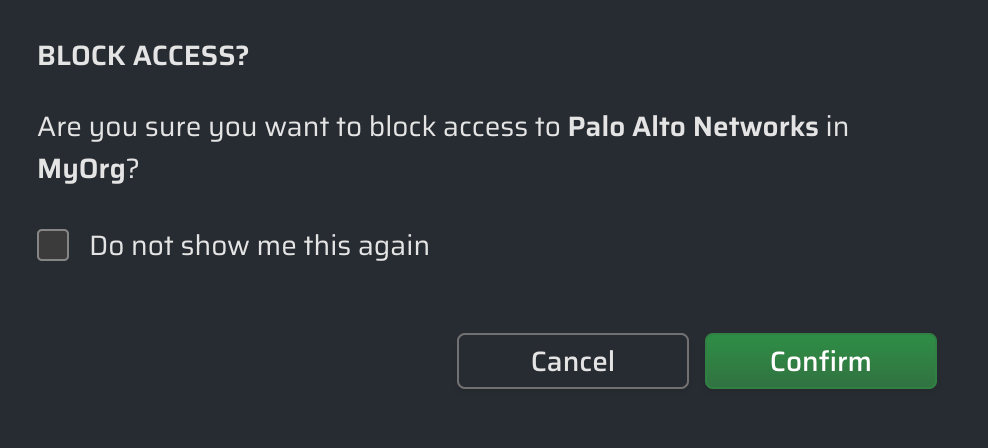
Blocking Third Party Access
Blocking access for a specific third party (to all accounts/resources for a selected scope) is as simple as:
- Clicking on the row of the third party you would like to block.
- Clicking on the confirmation dialog.
- Deploying those newly staged Pending Changes.
Renaming Third Party Entries
To rename a third party entry, click on the pencil icon within the row of the third party you would like to rename it:
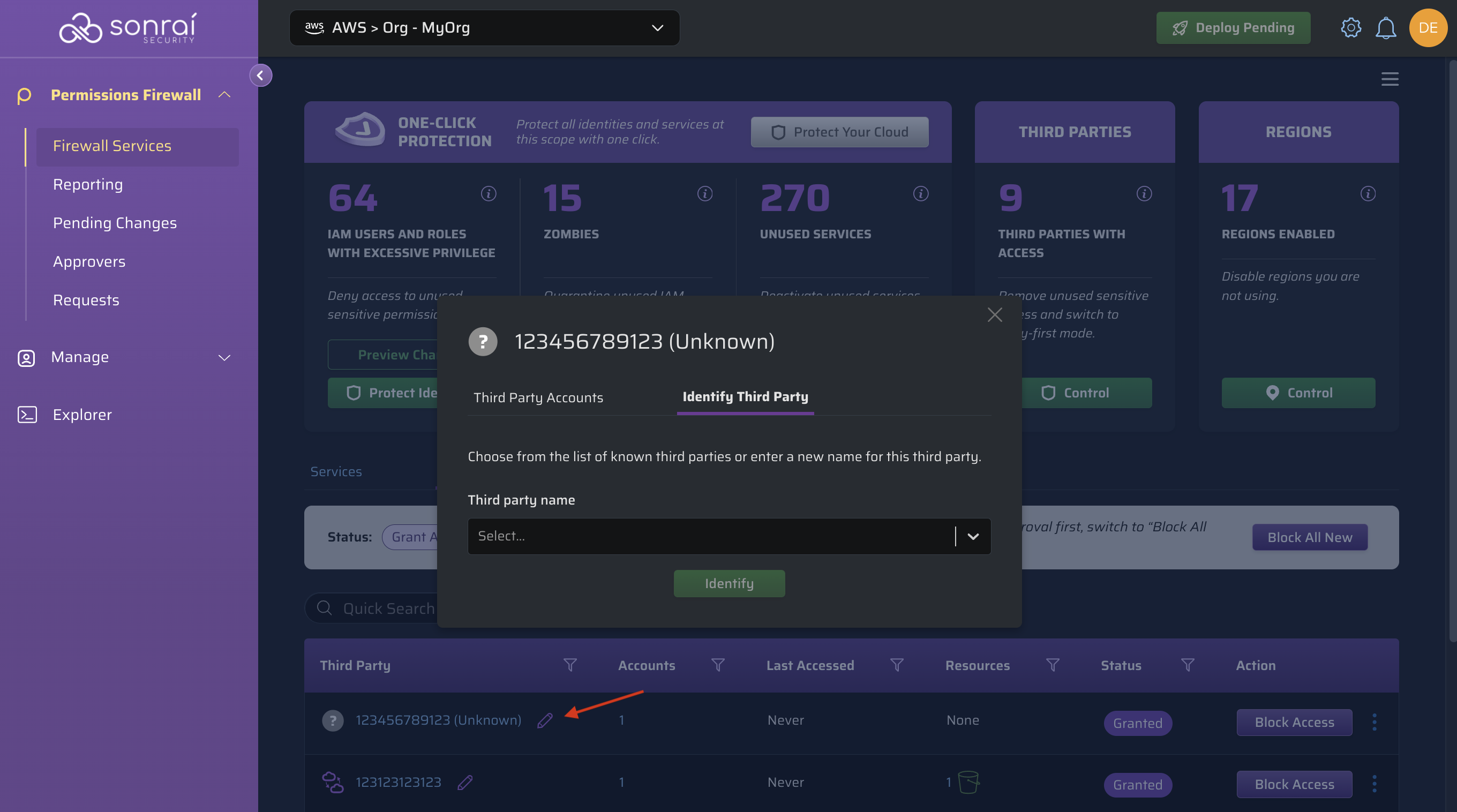
Next, you can choose from Sonrai's third party catalogue:
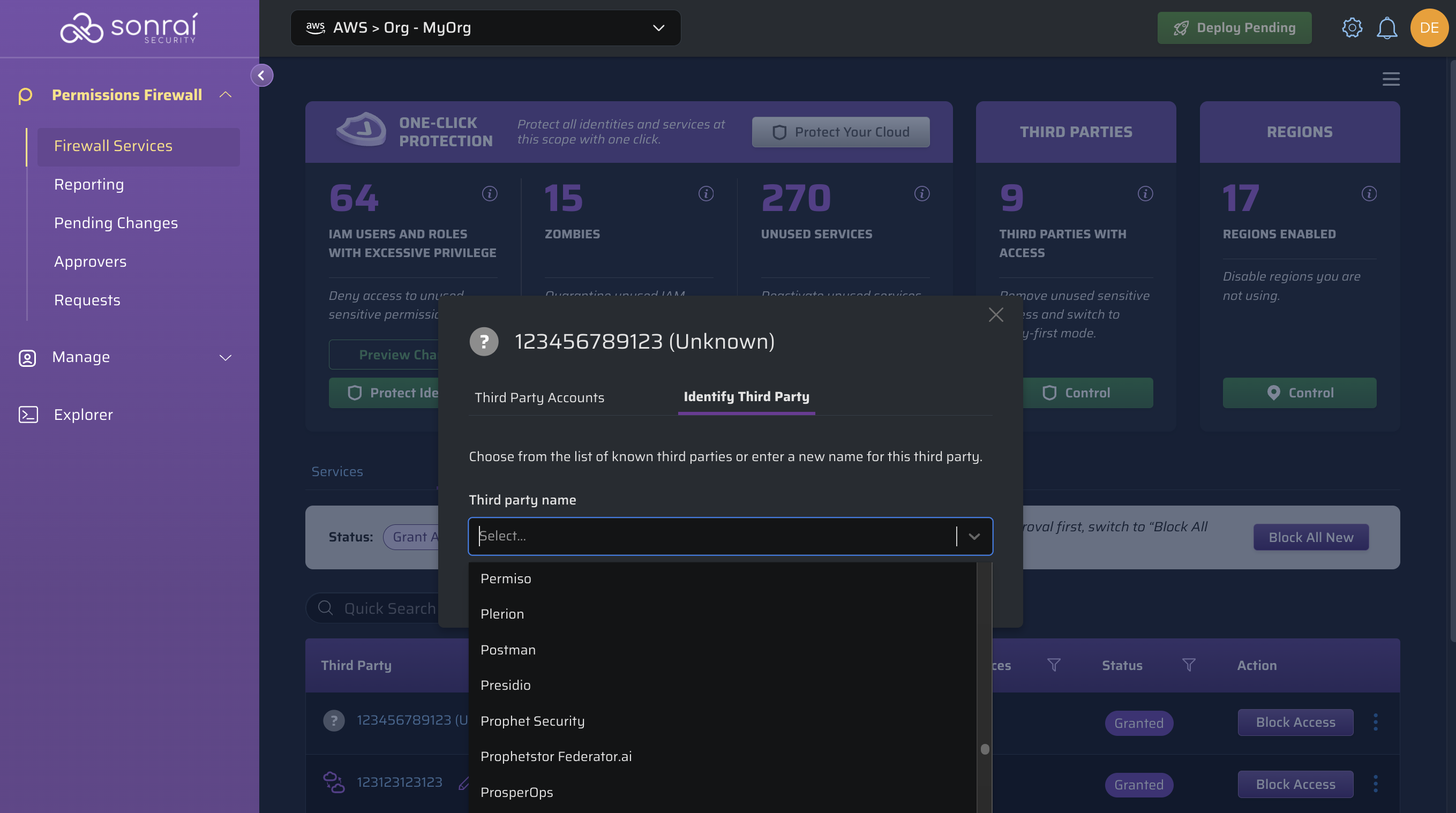
Or create a name for your new third party:

In the third party accounts tab, you will see all accounts identified as belonging to this third party:
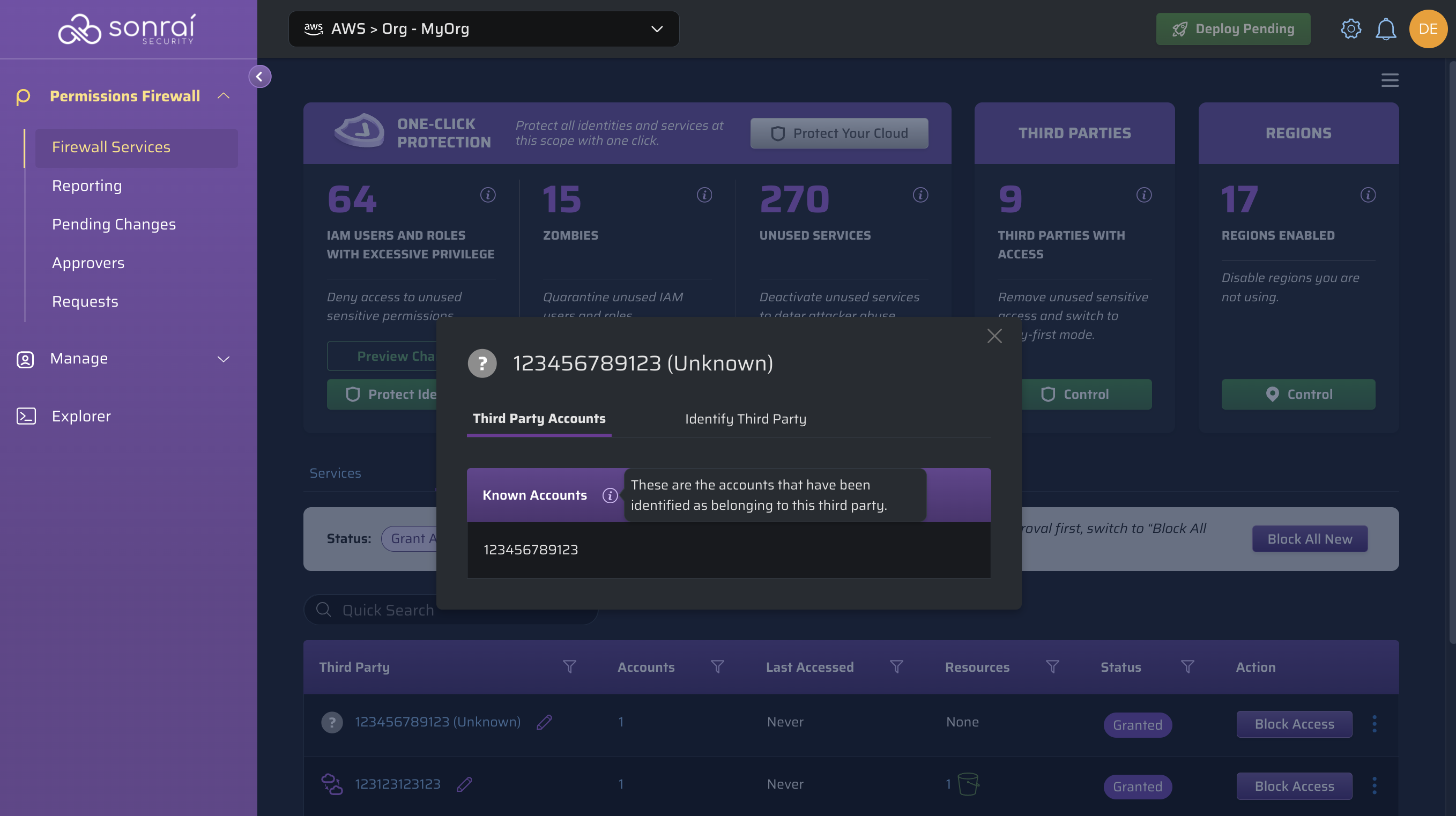
You can add more 'unknown' accounts to any third party within the catalogue (Sonrai's or your custom third parties) to see the account(s) show within this tab, as desired.
Third-Party Detection
Third-Party Account drift detection automatically monitors your AWS environment for new external (third-party) AWS accounts that gain access to your cloud resources through trust relationships.
When detected, Sonrai notifies the appropriate administrators so they can quickly review and validate that access. This helps maintain visibility, security, and governance over external account access.
What This Feature Does
When a new third-party AWS account appears in a trust policy or role assumption relationship, Sonrai:
- Detects new third-party accounts referenced in resource policies
- Determines whether access is granted or denied based on Cloud Permission Firewall (CPF) configuration
- Verifies discovery through IAM discovery jobs
- Notifies users with the appropriate permissions
- Records metrics for monitoring and auditing
Key Capabilities
Automatic Detection
New third-party AWS accounts are identified automatically as part of policy evaluation and access analysis.
Smart Notifications
Notifications are sent only to users with the required permissions, reducing unnecessary alerts.
IAM Discovery Integration
When new third-party accounts are detected, Sonrai automatically runs IAM discovery to validate and enrich the findings.
Resilient Processing
Built-in retry mechanisms help ensure reliable detection and notification, even during transient failures.
Configurable Processing Lag
A short, configurable delay (default: 6 minutes) allows related changes to be grouped before notifications are sent.
Notifications
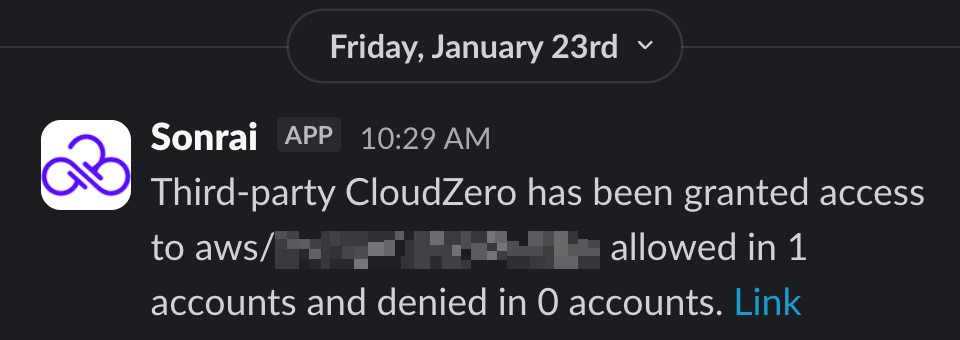
When a new third-party account is detected, Sonrai generates a ChatOps notification that includes:
- The third-party account name and AWS account ID
- The affected environment or root scope
- Whether access is granted or denied
- Counts of allowed and denied accounts
- A direct link to review the account in the Cloud Permission Firewall UI
Example Slack Notification
Notifications are sent only to users who have both of the following permissions at the relevant scope:
edit.cloudhierarchyedit.cloudcontrols
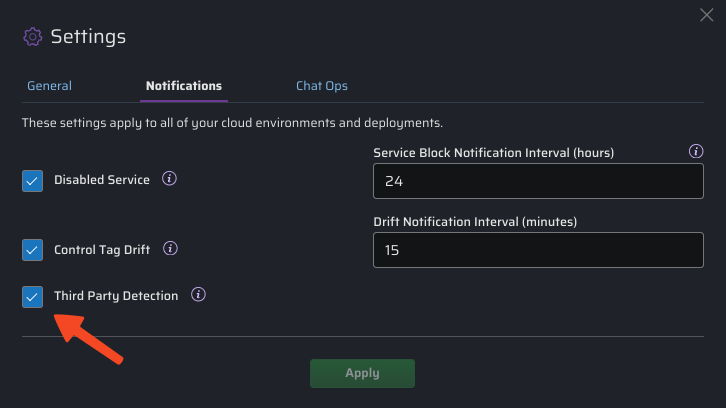
Disabling Third-Party Notification
This feature can be disabled or re-enabled for all organizations in your CPF deployment using the global system settings menu:
FAQ
What if there is no access control in place for a third party?
The state defaults to granted.
Why is the third party showing as 'Unknown'?
If both name and iconId are blank, we label the Third Party as "Unknown" and display only the ID.