Hero Card: Unused Services
© 2026 Sonrai Security. All rights reserved.
Overview
Unused services provide an easy way for attackers to create and modify resources, as well as an unintentional method of internal employees driving up costs by using services which have not been authorized by the business.
Examples
- Example 1: When Outsiders Become Insiders
- Example 2: When Insiders Cause Problems
Example 1: When Outsiders Become Insiders
One day, an attacker socially engineered their way into an AWS organization.
With the role to which they had gained access, they discovered an unused service, Amazon RDS. Within it, they were able to launch a stagnant RDS instance that had not been updated for several months and lacked recent security patches. Exploiting the present vulnerabilities, the attacker was able to gain unauthorized access to the organization's database.
With this access, the attacker explored the company's cloud infrastructure and quickly located sensitive patient data stored in an unprotected database. The attacker began exfiltrating this data and attempted to cover their tracks by modifying logs and access permissions.
Example 2: When Insiders Cause Problems
A company began experiencing unexpected service outages and performance issues in its network management systems. Customers reported difficulties accessing certain features and functions, while internal teams struggled with unexplained delays in processing data.
The IT team immediately began investigating the source of the issues. After a thorough review of the cloud environment, they traced the problem to a set of inactive services with scheduled lambda functions that had remained enabled but unused for several months. These services were once vital components of older applications but had since been replaced by newer, more efficient versions. However, the old services were never fully shut down and remained referenced by the system.
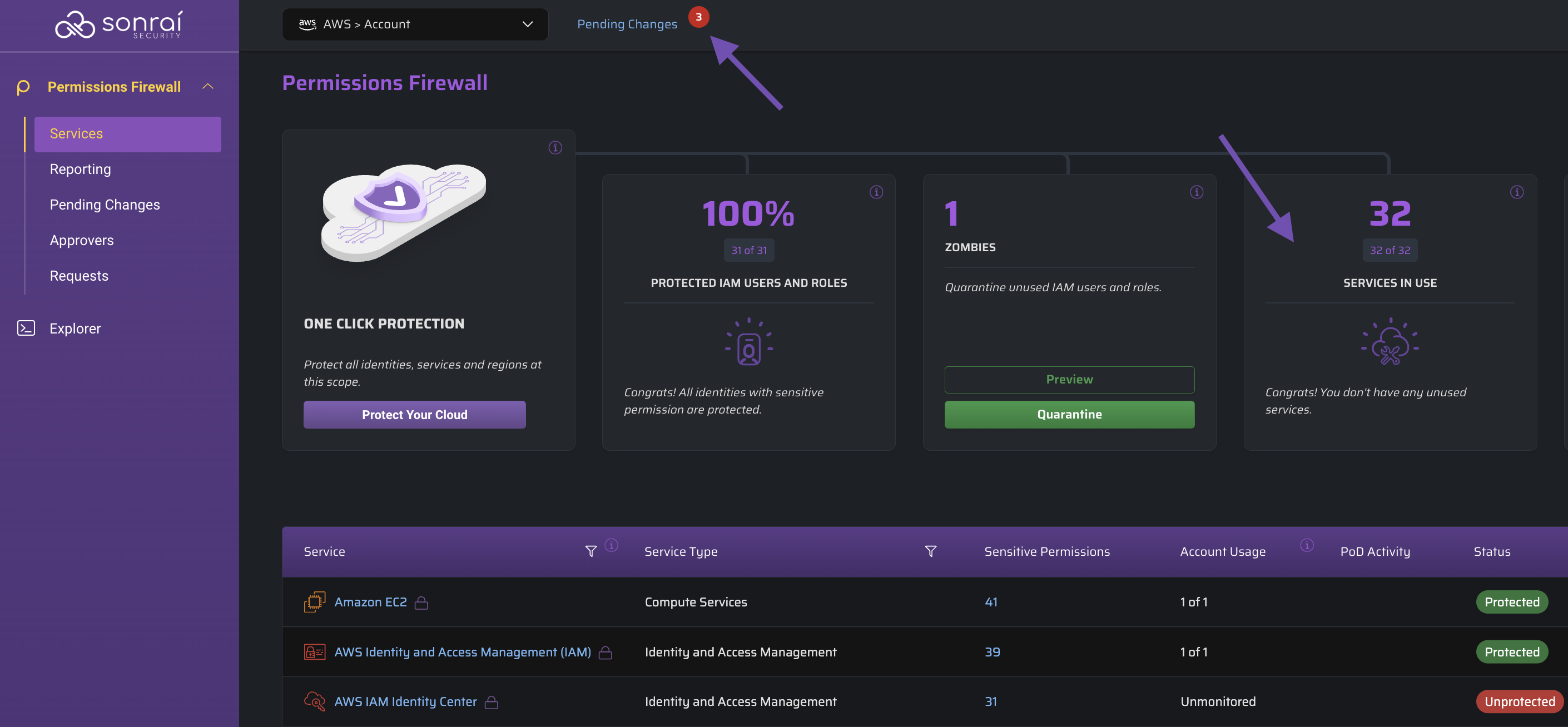
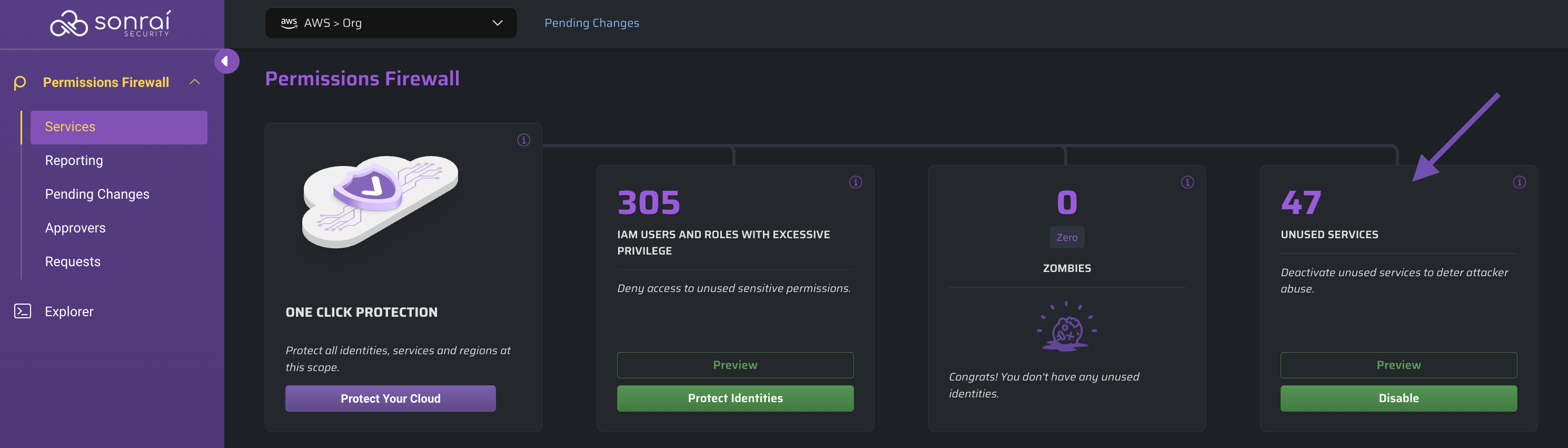
Disable Your Unused Services
Select the scope at which you want to take action and click the button to see the changes you are about to make:
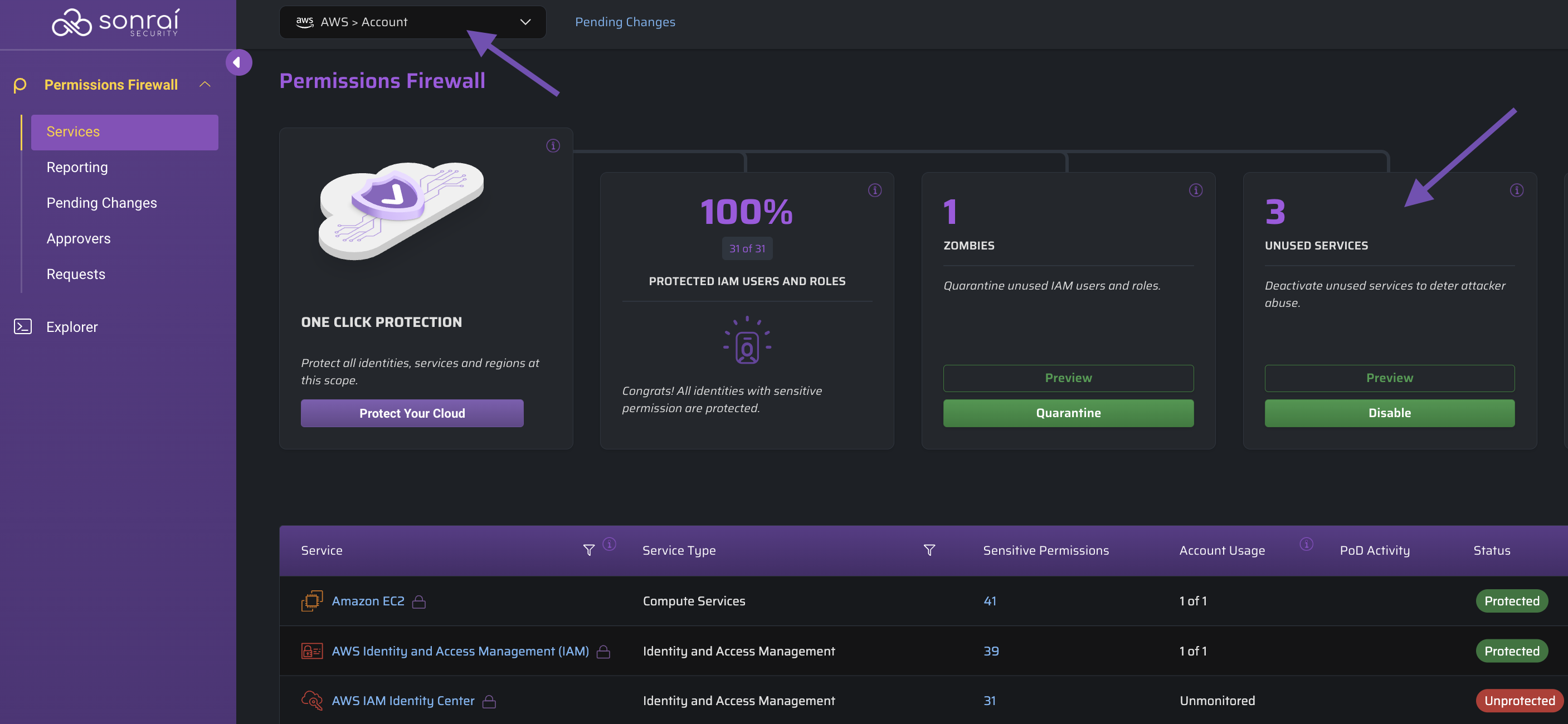
When ready, click the button to review those changes within the Pending Changes page before you deploy them to your cloud: