Reporting & Audit Information
© 2026 Sonrai Security. All rights reserved.
Overview
The Reporting section provides an overview of exceptions/exemptions that have been implemented for specific accounts (authorized users, break glass accounts, etc.) and a detailed audit log tracking user interactions with the Cloud Protection Firewall.
- Exemption List
- Detailed Audit Log
Exemption List
Exception
The identity for which the exemption has been made
Service
The service for which the exemption applies
Approval Date
The date/time at which the approval has been granted
Approver
The Approver who authorized the exemption
Permissions
The privileged permissions which were approved for use by the identity
Scope
The scope at which the service's privileged permissions apply for the identity in question
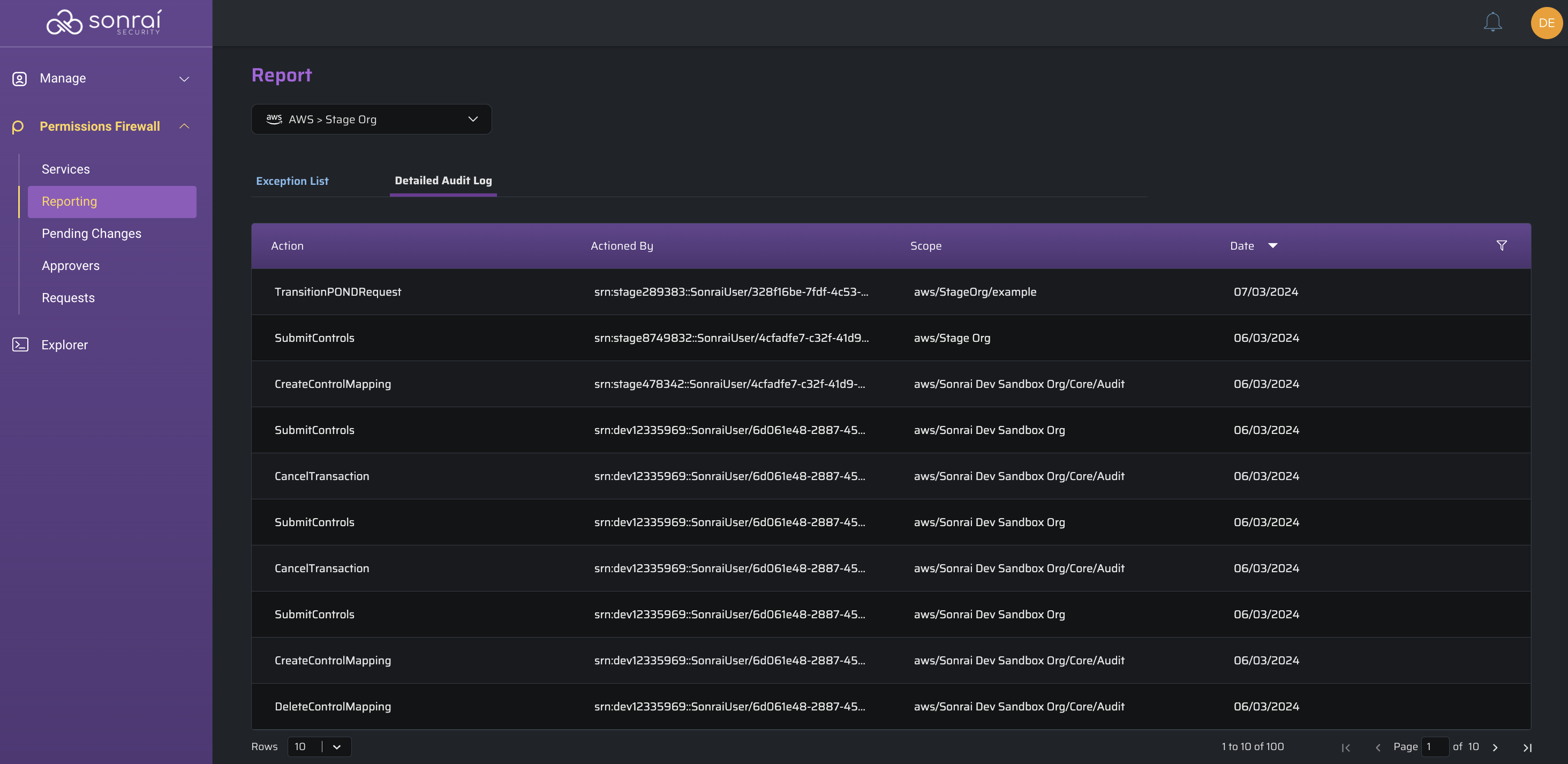
Detailed Audit Log
Action
The action that was taken by a Cloud Permissions Firewall (CPF) user
Actioned By
The user that completed an action
Scope
The scope at which the action occurred
Date
The date on which the action occurred
Exemption List
Service-based exemptions will be made for identities within your organization which require continued access to privileged permissions, and those exempted identities will be listed for reference on this Reporting page.
Some of these identity exemptions will be facilitated through the Services slide-in panel for a specific service/account, while other exemptions will be made through Permissions on Demand (POD) requests.
The roll-up widgets provide metrics for top trending POD requests (involved user, service, scope) and request approvals versus denies.
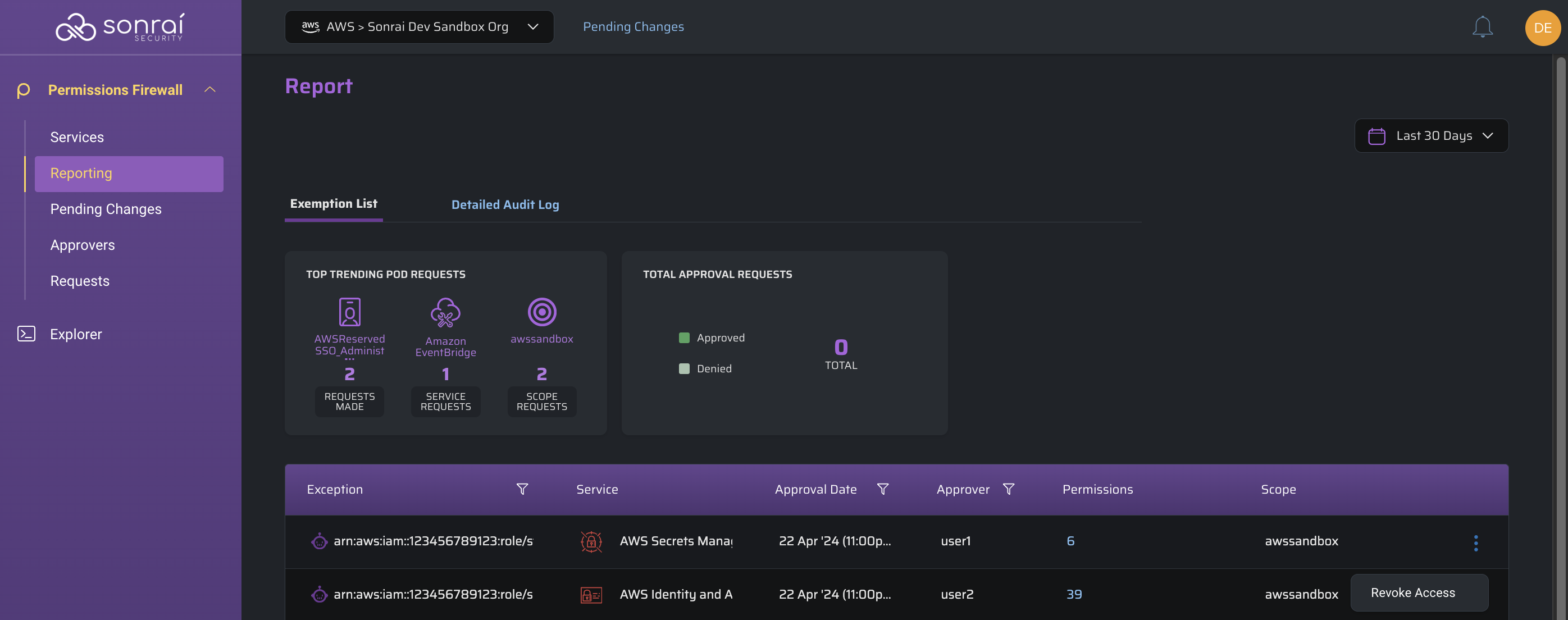
Click the 3 dots menu on the right to Revoke Access (i.e. remove this identity exemption for this set of privileged service permission(s))!
Privileged Permissions Identity Exemptions
When you protect a service, you can add exemptions to each account in scope to ensure no disruption in operations occurs. The most common use case(s) include machine identities used to deploy infrastructure or break glass identities.
Reference: See here for more information on the "Protecting Services & Exempting Identities" page.
Detailed Audit Log
Along with stating the action that occurred, the user that performed the action, the scope at which the action was performed, and the date and time at which the action occurred is present for each table row to provide you with a contextual timeline of events.
When viewing the audit log, below are some inclusions you may encounter:
| Action | Description |
|---|---|
CreateControlMapping | A service has been protected or disabled |
DeleteControlMapping | A service has been unprotected |
AddExceptionIdentity | An identity has been exempted from a service protection |
RemoveExceptionIdentity | A previously exempted identity has been removed from a protected service exemptions list |
SubmitControls | The "Pending Changes" are translated to the CloudFormation template (json file) |
The time range can be changed using the filter in the top right hand corner to quickly narrow down results.