Approving/Denying Permissions on Demand Requests
© 2026 Sonrai Security. All rights reserved.
Overview
Permissions on Demand (PoD) requests are routed through email or ChatOps (Slack/Teams) to the relevant Approvers at scope.
Protected Services
- If a user logged into AWS using IAM Identity Center attempts to perform an action involving a protected privileged permission AND they can be reached via Sonrai ChatOps in Slack or Teams:
- They will be presented with a Justification request including a requested time interval for their use of the permission
- Once submitted, this request will be routed to the Approver(s) at scope
If the user requesting privileged permissions usage is also an Approver for that AWS account, they will only be presented with the Approval request to avoid having to justify and approve the same action
- If no action is taken within an hour (i.e. no approval or denial), an additional notification is sent to the user(s) in the next level up in the Approvers tree
- To action these requests, users are transported from the email into the Cloud Permissions Firewall Request page or directly in ChatOps (Slack / Teams)
- If no approval or denial is completed within a 24 hour period, the Request expires and will be resubmitted on the user's next unprivileged attempt to use that privileged service permission
Disabled Services
- If a user logged into AWS using IAM Identity Center attempts to access any permission of a disabled service AND they can be reached via ChatOps in Slack or Teams, a ChatOps message will be sent to the user to notify them that the service is disabled
This message cannot be sent for activities that AWS does not Audit
Prerequisites
Ensure the Approver has the "Cloud Permissions Firewall Approver" [or "Administrator"] RBAC role assigned.
Permissions on Demand (PoD) Request Statuses
| Status | Description |
|---|---|
| Requested | The privileged service permissions access was requested by the identity. This action begins a 24 hour timer, after which if no action is taken the request will expire. Relevant to ChatOps:
|
| Pending | The privileged service permissions access request is pending (the Approver(s) have not approved or denied the Request yet, and the 24 hour expiry timer is reset). |
| Approved | The privileged service permissions access request was approved, meaning the user can now use the requested permissions |
| Denied | The privileged service permissions access request was denied, meaning the user still cannot use the requested permissions |
| Expired | The Request itself expires in 24 hours if not actioned. |
| Abandoned | Relevant to ChatOps, the user clicked "No" to providing required justification for the requested privileged permissions access |
| Abandoned (expired) | Relevant to ChatOps, the user did not provide the required justification for the requested privileged permissions access within 24 hours |
Permissions on Demand Requests
The "Requests" page table view provides information on each Permissions on Demand request made by users.
A user's view of this page will differ based on the scope at which they are granted to authorize Requests (i.e. Org level, OU, account).
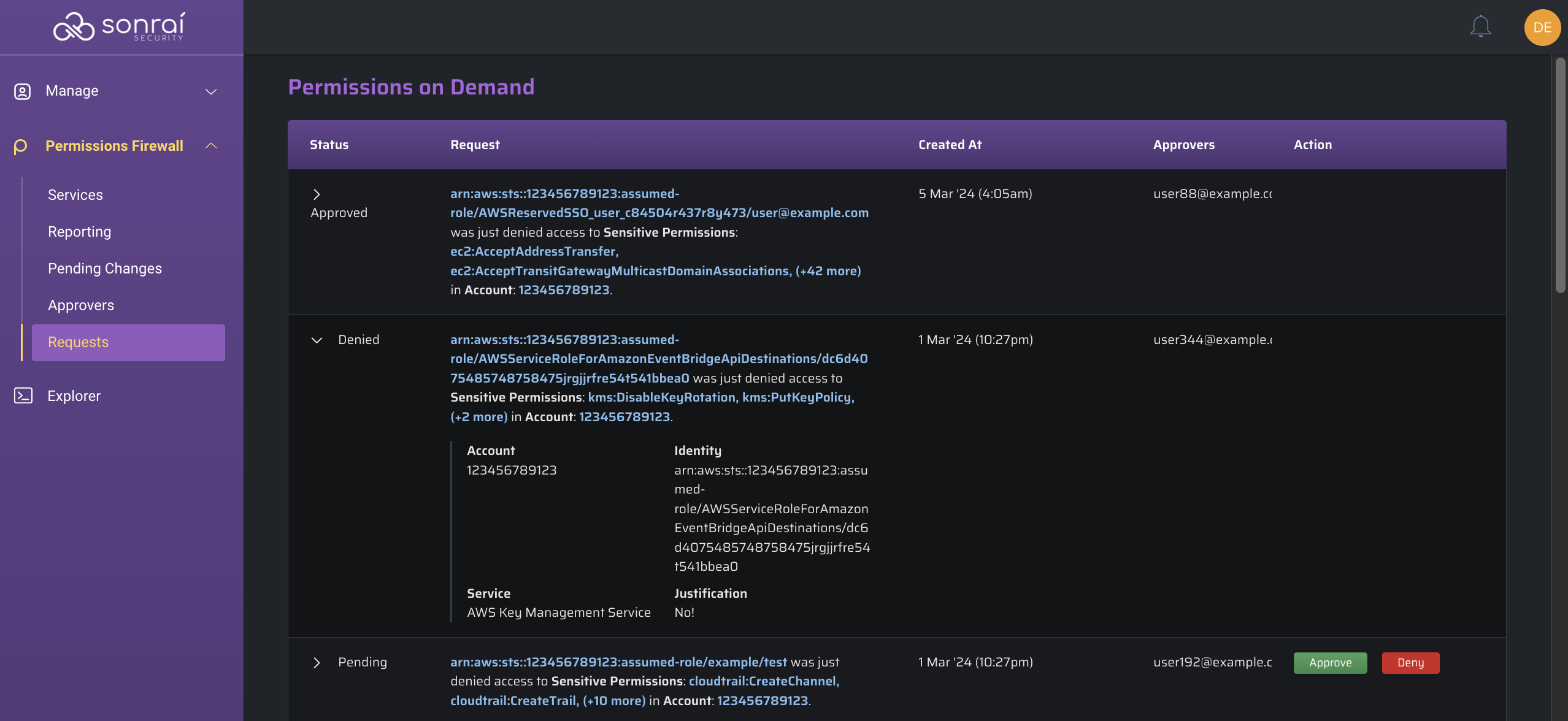
Status
The status of the request (approved, denied, etc.)
Request
A summary of the request for permissions that has been made
Created At
The date/time at which the request had been made
Approvers
Applicable Approvers that can approve the request
Action
The applicable actions an Approver may take (approve/deny)
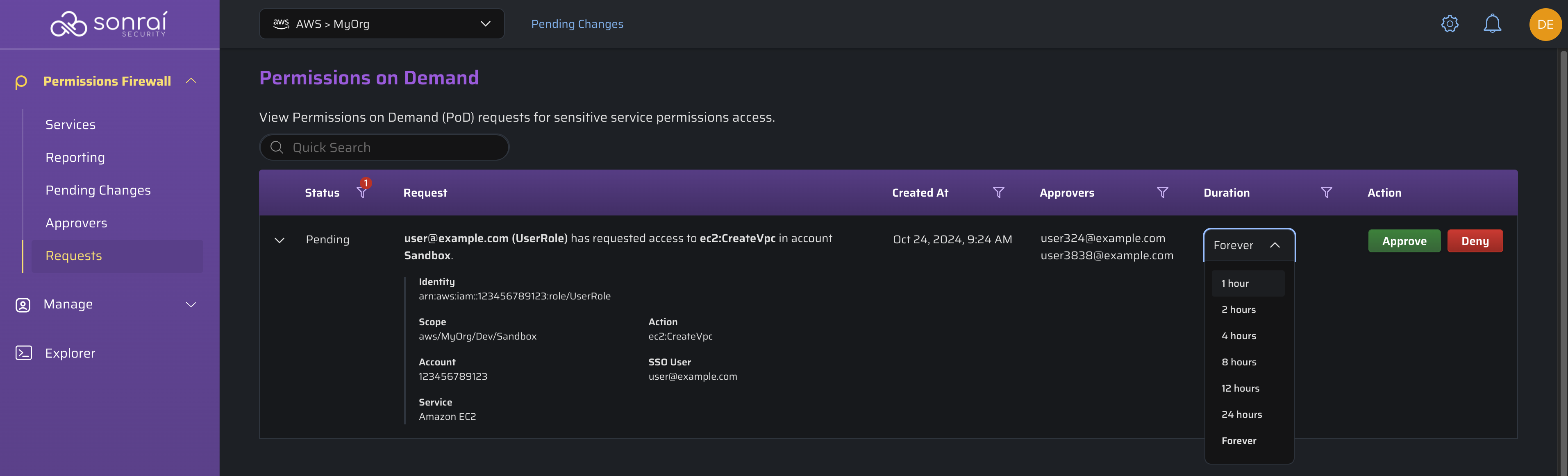
Approving & Denying Cloud Permissions Firewall Requests
Once you click the link you have received within the email, your view will transfer to the Cloud Permissions Firewall UI > Requests page with that request in focus.
Generally speaking, there are two actions:
- Approve: Review and confirm the requester is authorized to use the requested privileged permission(s)
- Deny: Review and deny the user access to the privileged permission(s)
Both actions require a message containing context/justification for approval/denial of the request.
Approval Durations (Timeboxing PoD Requests)
You may want to limit the amount of time a user has access to privileged service permissions and that's where timeboxing for the Permissions on Demand Request comes in.
For Permissions on Demand approvals and/or timeboxing overrides, the Approver must have either the Admin role or the Cloud Permissions Firewall Approver role assigned.
If the cog menu Settings in the top righthand corner > Request User Justification box is not checked, users will not see either the justification text box or approval timeframe dropdown menu within the request.
Approvers can still set an approval duration without the Request User Justification box checked (and without ChatOps configured)!
When a user spurs a Permissions on Demand Request for an enabled, but protected, service, the request requires a duration (default: forever).
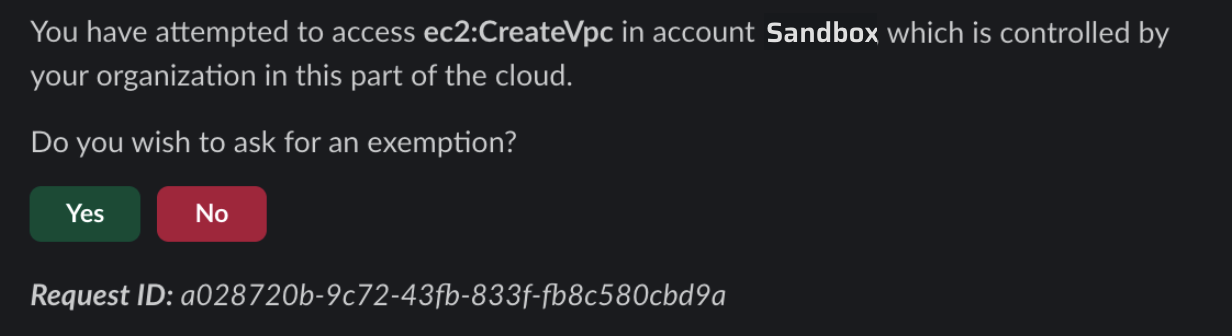
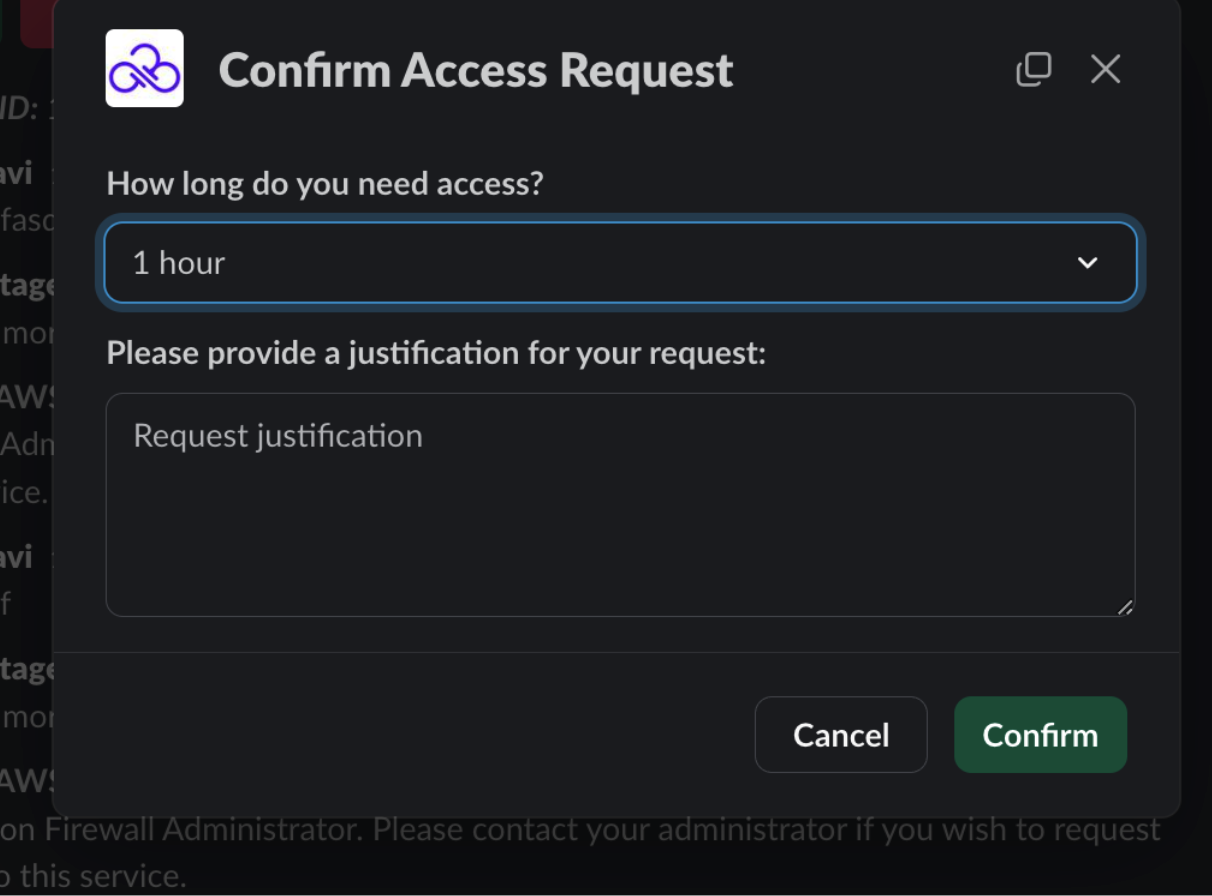
Approvers can override the duration the user has requested (in either Teams/Slack or the Sonrai Requests page), if needed. Simply choose an alternate duration for the user's privileged permission(s) access and click :
Once the approval timeframe has completed, the privileged service permissions access is revoked and the user will receive an error message similar to:
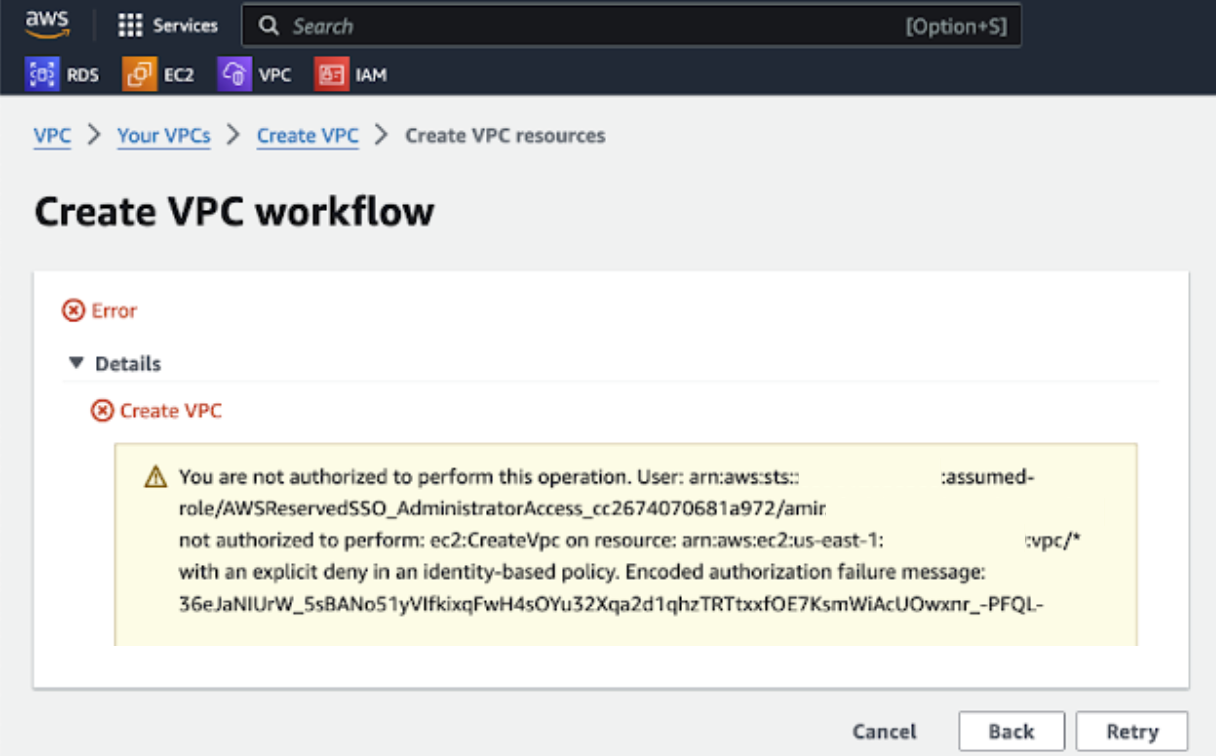
Users can make an additional Permissions on Demand Request for more time, if needed.
Permission(s) granted via Permissions on Demand (PoD) for a set duration will be revoked during the 5 minutes following its expiration.