Cloud Permissions Firewall Troubleshooting
© 2026 Sonrai Security. All rights reserved.
Overview
As a Sonrai Cloud Permission Firewall (CPF) Administrator, you need to know how to avoid access lockouts and be able to safely restore access if CPF ever experiences degraded performance or becomes unavailable. Don't worry — we’ve got this covered.
This page gives detailed instructions about how to troubleshoot issues, or even temporarily switch off CPF through AWS if needed. Start with the least‑impactful scenario and escalate when required.
Before taking actions described on this page, always contact Sonrai Customer Success to let us know about your issues. We're here to help!
Scenario 1:
The Sonrai Web App is responsive, but you must temporarily remove all CPF controls...
- Remove Controls using Sonrai CPF.
- Recovery & Re‑Sync process to restore your CPF deployment.
Scenario 2:
The Sonrai Web App is not responding, and you need to remove all CPF controls (outage)...
- Perform an Emergency Stop from AWS.
- Remove Controls using Sonrai CPF.
- Recovery & Re‑Sync process to restore your CPF deployment.
Emergency Stop from AWS
In rare cases, the Sonrai CPF application may be unavailable or unresponsive - preventing you from removing controls using the web interface. In this scenario, an emergency stop script is available to quickly disable Sonrai policies.
Temporarily removing controls will reduce protections and guardrails in your system. After using the emergency stop script, you must have a CPF administrator Remove Controls using Sonrai CPF and then complete the Recovery & Re‑Sync Controls process to restore protections.
Prerequisites
- Access to the AWS Management Account (or delegated admin with equivalent rights).
- Ability to download from the Sonrai S3 bucket in your Management Account.
Locate Your Emergency Stop Script
- Sign in to your AWS Management Account (or delegated administrator account).
- Locate the Sonrai S3 bucket with a naming pattern similar to:
s3://sonrai-crc<OrgId>-<YourManagementAccountId>
- Inside the Sonrai S3 bucket, navigate to:
org/crc<OrgId>/cfTemplates/ - Scroll down to find and open the most recent object (excluding
current). - Download the
SonraiCPF.ziparchive. - Extract the
CPFEmergencyStop.pyPython file from this archive.
Execute An Emergency Stop
With your Org/Management Account environment (or using AWS CloudShell, if you do not have the AWS CLI set up), run:
python CPFEmergencyStop.py --action stop
You will be prompted to confirm that you want to remove all CPF controls, after which the script detaches all Sonrai‑named CMPs, SCPs, and RCPs.
After using the emergency stop script to detach policies, your organization will not have any Sonrai protections in place until a CPF administrator completes the following steps:
Be sure to complete these additional steps as soon as possible to restore protections.
Remove Controls using Sonrai CPF
You can use the CPF application to remove all applied policy changes from your cloud environment.
Removed controls are preserved as Pending Changes, so that your configuration can safely be re-deployed after the issue has been resolved. Do not delete the resulting Pending Changes after resetting CPF; you’ll use these changes to restore the configuration.
Temporarily removing controls will remove protections and guardrails in your system. Be sure to complete the Recovery and Re-Sync Controls process as soon as possible to restore CPF controls.
Prerequisites
- Ensure that you are logged in to AWS using your management account. (Making changes to the CloudFormation template for CPF relies on being logged in with an administrator role.)
- In the Cloud Permissions Firewall app, ensure that you have the correct organization selected.
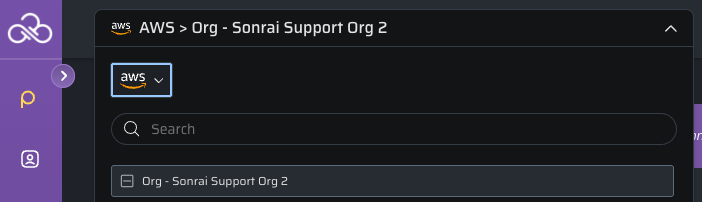
- To remove the protections you have deployed to one of your organizations, open the menu while viewing Firewall Services for that organization, and click the Remove Permissions Firewall from the Org <your organization> option.
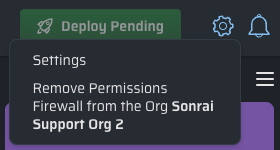
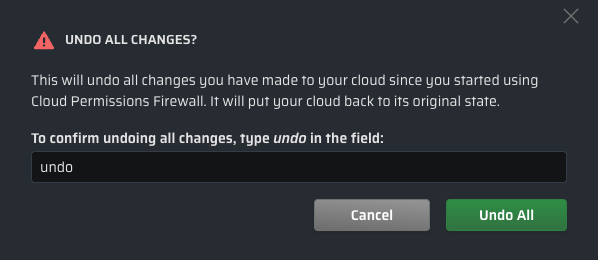
-
Confirm that you want to proceed by typing
undoin the text field and clicking .This triggers the removal of all elements from Cloud Permissions Firewall in your cloud, reverting it to its original pre-firewall state.
-
If CPF controls have been deployed previously, then you will be prompted to remove the
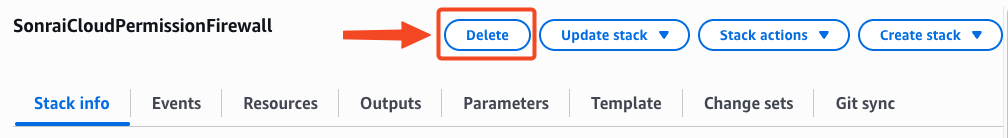
SonraiCloudPermissionFirewallstack in AWS CloudFormation.Click the provided link to be taken to your CPF CloudFormation Stack directly, or locate your stack manually in CloudFormation.
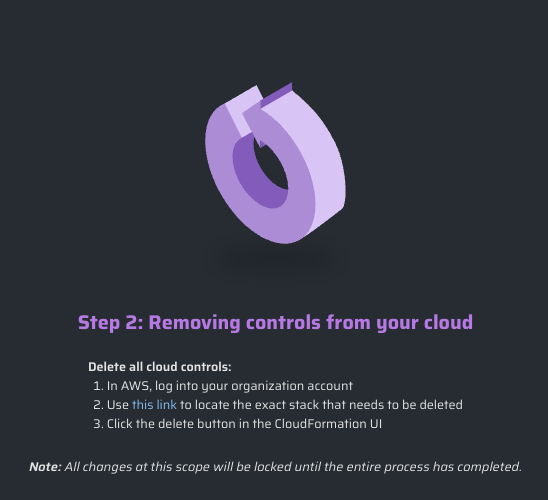
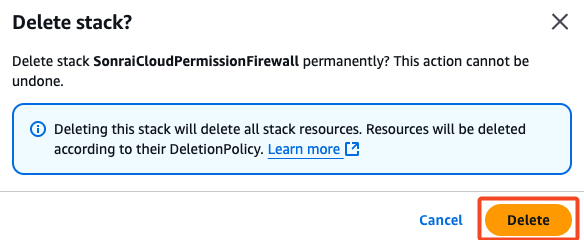
- Delete your CPF Stack in AWS CloudFormation.
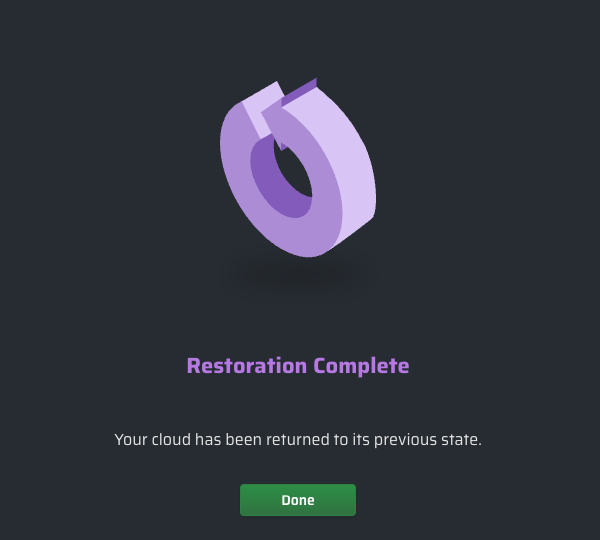
- Cloud Permissions Firewall has returned your environment to its original state. Click when the process is finished.
Any control and policy changes that were rolled back are now available as Pending Changes that you can then review, remove, or redeploy as desired.
Recovery & Re‑Sync Controls
After taking any emergency action where CPF controls are temporarily disabled, it's important to re-sync and restore your controls from Pending Changes to ensure your cloud environment is protected.
- Redeploy CPF controls from Pending Changes:
- In your Sonrai web application, open the Pending Changes view
- Click to re-sync existing controls, or if you removed controls using the CPF application.
- Monitor for successful apply across accounts
- Verify access and guardrails:
- Confirm that identities regain Just‑in‑Time and Permission on Demand access
- Spot‑check in target accounts/services
- Close the loop with Sonrai Support: Reach out and provide an incident summary and timing, helping us to prevent problems from reoccurring.
Break Glass Readiness (Preventative Measure)
Once CPF protections are back in place, you might want to set up a specific set of identity exemptions that can be used in the event of emergency. Two options are provided below; reach out to Sonrai Customer Success to discuss other implementations for your specific needs.
Option 1: Create a scoped exemption at the top of your Org
Some customers choose to exempt the OrganizationalAccessRole. Example pattern in Exempt at Scope menu:
*e/OrganizationalAccessRole
Option 2: Exempt an SSO User
Another option is to exempt an SSO user that maps to an Administrative Permission Set in all accounts. You do this the same as the above example by creating a scoped exemption at the top of the Org and choosing SSO User.
Learn more about how and why you might want to exempt identities from CPF protections.